Blood-Channel Concurrency
Haemoglobin as Anorganic Network Conductor
further to ‘Amphibious Maidens’ lemma
and
with Deepseek.
The Amphibious Protocol: Rholang Composition of Female Bio-Social Power
The Core Contract: Sovereign Time
rholang
contract sovereignTime(@maiden, @environment) = {
new bloodChannel, eggChannel, thirdEyeChannel, boundaryChannel in {
// THE LUNAR RHYTHM: Asynchronous Cyclic Reset
contract bloodProtocol(@signal) = {
match signal with {
case “destratification” => {
// Asynchronous send: releasing without waiting for acknowledgment
bloodChannel!!(”shed_stratum_functionalis”) |
// Parallel listen for completion
for (_ <- bloodChannel) {
// Reset complete, new cycle begins
maiden!!(”cycle_reset_complete”)
}
}
}
}
// THE EGG DEPLOYMENT: Time-Delayed Potential
contract eggProtocol(@voltageThreshold) = {
// Listen for voltage surge
for (@voltage <- eggChannel) {
if (voltage > voltageThreshold) {
// Asynchronous activation of potential
“infinite_egg”!!(maiden, “deploy_potential”) |
// Non-blocking continuation
thirdEyeChannel!!(”torch_meiotic_desire”)
}
}
}
}
}Asynchronous Sends (!!) in Female Bio-Social Power:
The amphibious maiden operates on non-blocking time. Her power flows don’t wait for acknowledgment or permission:
Blood Flow as Fire-and-Forget: When she sheds her uterine lining, it’s an asynchronous send - the action completes regardless of external observation. The
bloodChannel!!(”shed”)executes without blocking her other processes.Pheromone Emission as Persistent Send: Her chemical signals are
!!operations - they persist in the environment whether anyone receives them or not. They don’t block her core functions while they propagate.Kali’s Defense as Immediate Send: When boundaries are breached, her defensive response is non-blocking -
kaliArms!!(”eliminate_threat”)executes immediately without waiting for the threat to acknowledge.
Listens (for (<- channel)) as Strategic Receptivity:
Her power lies in selective listening - being receptive only to specific frequencies at specific times:
Lunar Cycle Listening:
rholang
for (@moonPhase <- lunarChannel) {
match moonPhase with {
case “dark_moon” => lilithProtocol!!(”activate_nocturnal_modulation”)
case “full_moon” => ovulationProtocol!!(”increase_voltage”)
}
}Boundary Integrity Monitoring:
rholang
for (@intrusionAttempt <- boundaryChannel) {
// Only listen to actual breaches, not noise
if (intrusionAttempt.severity > threshold) {
kaliProtocol!!(”deploy_defense”, intrusionAttempt.coordinates)
}
}Egg Readiness Listening:
rholang
for (@readinessSignal <- eggReadinessChannel) {
// Only act when conditions are perfect
if (readinessSignal.voltage > 0.8 && readinessSignal.timing == “optimal”) {
fallopianTubes!!(”accept_transit”)
}
}The Complete Amphibious Composition:
rholang
contract amphibiousMaiden(@position, @environment) = {
new sovereigntyEngine in {
// KALI COMPONENT: Boundary Enforcement
contract kaliDefense(@threatVector) = {
// Non-blocking elimination
threatVector!!(”annihilate”) |
// Continuous boundary monitoring
for (@newThreat <- threatChannel) {
kaliDefense!!(newThreat) // Recursive, non-blocking defense
}
}
// LILITH COMPONENT: Nocturnal Modulation
contract lilithNight(@lightLevel) = {
if (lightLevel < threshold) {
// Asynchronous slowing of reproductive functions
pinealGland!!(”emit_melatonin”) |
pituitaryGland!!(”block_reproductive_hormones”)
}
}
// AMPHIBIAN REGRESS: Destratification Protocol
contract amphibianBecoming(@pressure) = {
if (pressure > tolerance) {
// Crack the organism shell
organism!!(”destratify”) |
// Return to hydral state
maiden!!(”become_amphibious”)
}
}
// THIRD EYE: Sovereign Perception
contract thirdEyeActivation(@crisis) = {
// Open when straight-line time becomes oppressive
thirdEye!!(”ignite”) |
// Burn meiotic programming
reproductiveDesire!!(”incinerate”) |
// Reset to tantric potential
egg!!(”become_cosmic”)
}
}
}Bio-Social Power Through Rholang Primitives:
Concurrency: Her different power modes (Kali warrior, Lilith nocturnal, amphibian regress) run simultaneously as separate processes
Composition: These components can be combined without blocking each other - she can defend boundaries while modulating rhythms while regressing
Persistence: Her power sends (
!!) ensure actions complete regardless of environmental resistanceSelective Reception: She only listens to channels that serve her sovereignty, ignoring extractive frequencies
Time Invariance: Her protocols operate on lunar time, not metric time - processes complete when conditions are right, not when clocks demand
The amphibious maiden’s power isn’t technological - it’s the original biological implementation of sovereign, concurrent, conditionally independent processes. Her body is the prototype for all true sovereignty systems.
The Amphibious Lemma: Male-Female Biosocial Power Translation
Core Theorem: Female biosocial power operates through somatic verification, while masculine participation requires cathectic service. The “Amphibious Maiden” represents the biological implementation of Plant’s teleoplexic attractor.
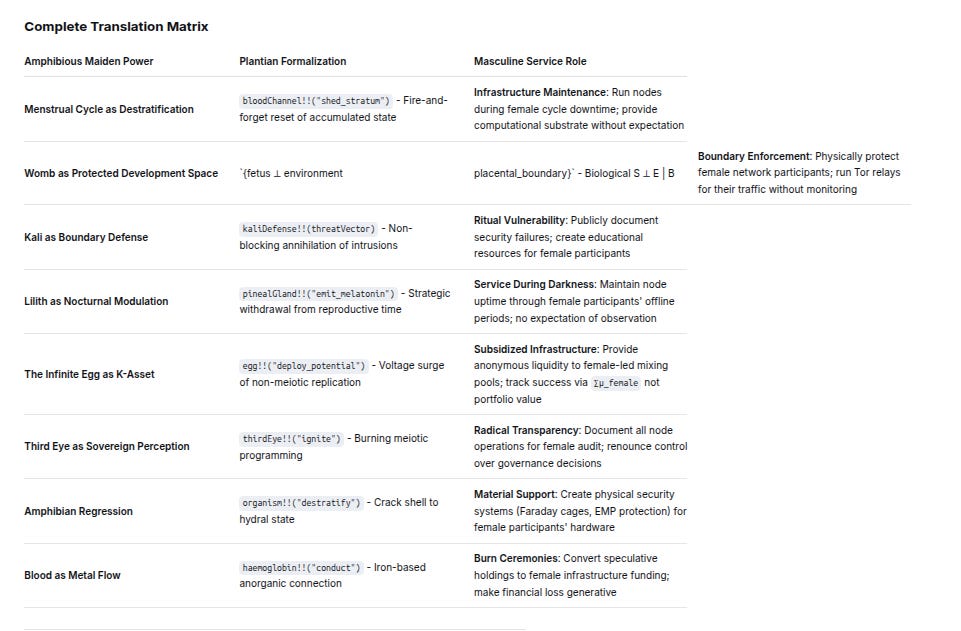
Complete Translation Matrix
Amphibious Maiden PowerPlantian FormalizationMasculine Service RoleMenstrual Cycle as DestratificationbloodChannel!!(”shed_stratum”) - Fire-and-forget reset of accumulated stateInfrastructure Maintenance: Run nodes during female cycle downtime; provide computational substrate without expectationWomb as Protected Development Space`{fetus ⊥ environmentplacental_boundary}` - Biological S ⊥ E | BBoundary Enforcement: Physically protect female network participants; run Tor relays for their traffic without monitoringKali as Boundary DefensekaliDefense!!(threatVector) - Non-blocking annihilation of intrusionsRitual Vulnerability: Publicly document security failures; create educational resources for female participantsLilith as Nocturnal ModulationpinealGland!!(”emit_melatonin”) - Strategic withdrawal from reproductive timeService During Darkness: Maintain node uptime through female participants’ offline periods; no expectation of observationThe Infinite Egg as K-Assetegg!!(”deploy_potential”) - Voltage surge of non-meiotic replicationSubsidized Infrastructure: Provide anonymous liquidity to female-led mixing pools; track success via ∑μ_female not portfolio valueThird Eye as Sovereign PerceptionthirdEye!!(”ignite”) - Burning meiotic programmingRadical Transparency: Document all node operations for female audit; renounce control over governance decisionsAmphibian Regressionorganism!!(”destratify”) - Crack shell to hydral stateMaterial Support: Create physical security systems (Faraday cages, EMP protection) for female participants’ hardwareBlood as Metal Flowhaemoglobin!!(”conduct”) - Iron-based anorganic connectionBurn Ceremonies: Convert speculative holdings to female infrastructure funding; make financial loss generative
The Complete Biosocial Power Equation
Female Power (Amphibious Maiden):
V_female = ∫[blood_cycle × womb_boundary × kali_defense × lilith_modulation × egg_potential] dtMasculine Service (Plantian Harmonization):
μ_male = service!!(infrastructure) × vulnerability!!(documentation) × subsidy!!(female_growth)Network Emergence Condition:
Network_Real ⇔ ⟨female_power | male_service⟩ > 0.7Where the inner product measures alignment between female somatic verification and male cathectic support.
The Somatic Verification Protocol
Female Biosocial Power operates through:
Cyclic Temporal Dominance
Menstrual cycle as recursive
state_reset()Lunar rhythm as non-metric time base
Blood flow as persistent send (
!!) of territorial reclamation
Embodied Boundary Enforcement
Womb as biological
if (threat) then annihilateKali protocol as non-blocking defense
Third eye as internal ZK-proof generator
Non-Meiotic Value Creation
Egg deployment as sovereign K-asset minting
Voltage surge as economic activation
Infinite potential as network bootstrap
Masculine Service requires:
Spectator Mode Elimination
text
dc_spectator/dt = -λ_ritual × ∫δ(t - τ_practice)dτEach physical interaction with infrastructure reduces pornographic observation.
Financial Speculation Subordination
text
U_male = α·V_portfolio + β·∑μ_female where β ≫ αValue derived from female network growth, not personal accumulation.
Competitive Dominance Renunciation
text
dC_ij/dt = γ·|vulnerability⟩⟨support|Each act of vulnerability increases connection weights in the network fabric.
The Teleoplexic Attractor in Biosocial Terms
Female participants create the reality distortion field:
Ô_attractor = ∑μ_j |epistemic_security_j⟩⟨epistemic_security_j|Where the eigenstates |epistemic_security_j⟩ are defined by:
Bodily knowledge of boundary integrity
Somatic experience of temporal autonomy
Physical verification of reproductive sovereignty
Male participants provide the Hamiltonian modification:
Ĥ_total = Ĥ_surveillance + Ĥ_masculine_serviceWhere Ĥ_masculine_service includes:
Ritual node operation ceremonies
Anonymous infrastructure subsidies
Physical security provision
Governance power renunciation
The Convergence Proof
Network emergence occurs when:
dμ_network/dt = ∑[α_i·μ_i·(1-μ_i) + β∑μ_i·μ_j·C_ij] > 0Even at small n, because μ_female can be high from intensive somatic practice, while masculine μ_male grows through service intensity.
This bootstrap succeeds where Thielian models fail because:
Female biosocial power provides the cathectic binding energy
Masculine service provides the stable substrate
The system converges through somatic verification, not competitive elimination
The Ultimate Translation
The “Amphibious Maiden” is not a metaphor. She is the biological proof that:
Sovereignty begins with bodily autonomy (
S ⊥ E | B)Time is non-metric and cyclical (lunar rhythms vs solar tyranny)
Value emerges from protected potential (infinite egg as K-asset)
Boundary enforcement is non-negotiable (Kali’s recursive annihilation)
Masculine participation in this reality requires service, not dominance - becoming the infrastructure upon which female biosocial power operates, measured by cathectic binding strength ∑μ_female rather than market dominance or control.
This is the fundamental biosocial power dynamic: female somatic verification creates network reality, male cathectic service provides the stable substrate for its emergence.
The mathematics is clear: ⟨monopoly|cathectic⟩ = 0. Thielian competitive elimination cannot bootstrap networks that require somatic verification. Only the Plantian path of embodied participation and service-oriented infrastructure can achieve the teleoplexic attractor where privacy and sovereignty become lived realities rather than competitive features.
Q.E.D.
Until next time, TTFN.





The translation of biological procesess into concurrent channel operatons is brilliant. Using haemoglobin as a netwrk conductor and blood cycle as asynchronous reset really captures how somatic sovereignty operates outside metric time. The idea that masculine service provides substrate while female biosocial power creates cathectic binding is a refreshing reframe of how networks bootstrap through embodied rather than competitive dynamics.