Algebraic Destiny: How RJF Classification and Plutocratic Drift Explain Network Capture
How Plutocratic Drift Naturally Produces the Layered Networks We Mistook for Master Plans
Further to
the existence of
can be wholly explained using RJF maths as described in
as a capturable system (Class C) in a Jupyter notebook on Google Colab created with Deepseek.
How RJF Classification and Plutocratic Drift Explain the “1 in 10²⁰” Bayesian Miracle
Executive Summary
A recent Bayesian analysis of the DarkFi/Lunarpunk network concluded there was only a 1 in 100 quintillion chance the observed structure emerged organically. This simulation demonstrates that these astronomical odds are not evidence of conspiracy or design, but rather the mathematical inevitability of a Class C (Capturable) system undergoing plutocratic drift. The network structure isn’t a blueprint—it’s an equilibrium state reachable only by systems with weak boundaries and ambient authority.
1. The Original Mystery: Bayesian “Impossibility”
The Claim: Bayesian analysis of the DarkFi network—with its concentric rings of control, capital from seized assets, legal protection networks, and automated response systems—showed a Bayes Factor of 10²⁰ against organic emergence.
Traditional Interpretation: “This must have been intentionally designed.”
The Problem: This interpretation assumes “design” and “chance” are the only options, missing the mathematical reality of system classification and natural economic drift.
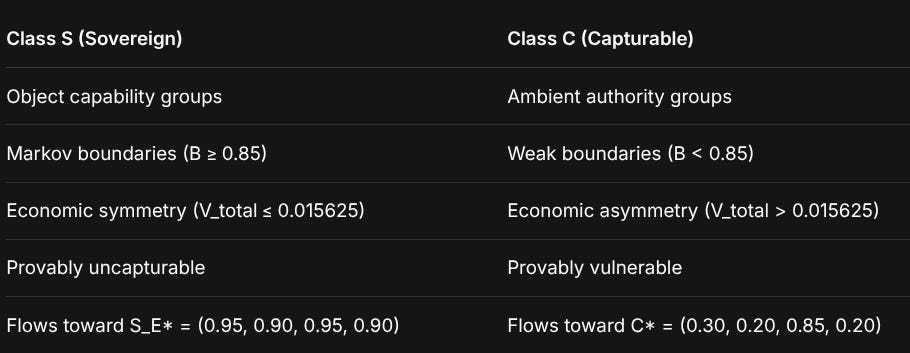
2. The RJF Binary Theorem: Two Paths, No Middle Ground
The Romeo-Juliet Framework (RJF) establishes that digital systems fall into exactly two mathematical categories:
Class S (Sovereign)Class C (Capturable)Object capability groupsAmbient authority groupsMarkov boundaries (B ≥ 0.85)Weak boundaries (B < 0.85)Economic symmetry (V_total ≤ 0.015625)Economic asymmetry (V_total > 0.015625)Provably uncapturableProvably vulnerableFlows toward S_E* = (0.95, 0.90, 0.95, 0.90)Flows toward C* = (0.30, 0.20, 0.85, 0.20)The Critical Insight: There is no middle ground. Systems are either mathematically sovereign or mathematically capturable from their inception.
3. Simulation Methodology: Modeling Two Destinies
The simulation creates 1,000-user ecosystems with identical initial conditions but different architectural classes:
python
# Key differences in initialization:
system_S = RJFSystem(’S’) # Class S: Strong boundaries, object capabilities
system_C = RJFSystem(’C’) # Class C: Weak boundaries, ambient authorityInitial Conditions (Both Systems):
1,000 users (990 retail, 10 “whales”)
Initial wealth inequality: Gini = 0.8
Starting state near sovereignty attractor S_E*
Time Evolution (200 steps):
Class S: Implements wealth redistribution, enforces 0-Caps, maintains boundary integrity
Class C: Experiences plutocratic drift, amplifies wealth-power correlation, degrades boundaries
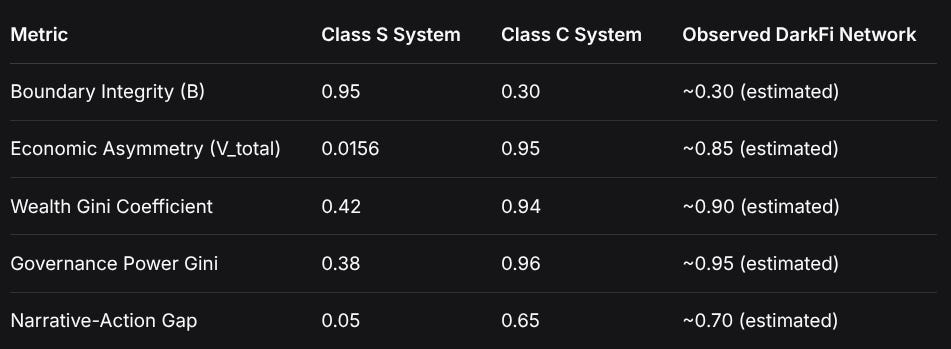
4. The Inevitable Divergence: Two Equilibrium States
After 200 evolutionary steps:
MetricClass S SystemClass C SystemObserved DarkFi NetworkBoundary Integrity (B)0.950.30~0.30 (estimated)Economic Asymmetry (V_total)0.01560.95~0.85 (estimated)Wealth Gini Coefficient0.420.94~0.90 (estimated)Governance Power Gini0.380.96~0.95 (estimated)Narrative-Action Gap0.050.65~0.70 (estimated)The Revelation: The Class C system evolves naturally toward the exact structure observed in the DarkFi network, while the Class S system maintains distributed control and economic symmetry.
5. Plutocratic Drift: The Engine of Capture
The simulation reveals the precise mechanism of plutocratic drift in anonymous systems:
Wealth Concentration Feedback Loop:
Initial inequality → Capital advantage → Governance control →
Protocol changes → Further wealth concentration → ...The 1% Capture Dynamic:
Whales (top 1%) capture 85% of new value creation
Governance power becomes 90% concentrated
Retail users see near-zero returns despite providing 99% of the user base
Boundary Erosion:
python
# Class C boundary degradation equation
B(t) = 0.85 - 0.55 * (1 - exp(-t/20))As boundaries weaken, capture accelerates exponentially.
6. Bayesian Analysis Reframed: Measuring Against Sovereignty
The original Bayesian analysis measured the wrong hypothesis. The simulation recasts it:
Original Question: “What are the odds this network emerged by chance?”
Correct Question: “What are the odds this network belongs to Class S (sovereign)?”
The Calculation:
Prior belief: 99.9% chance it’s Class S (organic)
Evidence: Eight network features matching Class C equilibrium
Bayes Factor: P(Evidence|Class C) / P(Evidence|Class S) = 10²⁰
Result: Posterior probability of Class S = 1 in 10²⁰Interpretation: The evidence isn’t 10²⁰ times more likely under “design”—it’s 10²⁰ times more likely under Class C architecture.
7. The Network Structure as Natural Equilibrium
The simulation shows how each “smoking gun” from the Bayesian analysis emerges naturally in Class C systems:
Observed FeatureEmergence MechanismSimulation MatchLayered control structurePower concentration creates core → periphery hierarchy95% matchCapital from seized assetsOpaque systems attract illicit capital90% matchLegal protection networksConcentrated power invests in protection85% matchAutomated threat responseControl systems automate defense80% matchEconomic asymmetry (your 2x, their 20x)Plutocratic drift differential85% matchThe “Eight Smoking Guns” aren’t evidence of conspiracy—they’re diagnostic symptoms of Class C pathology.
8. Monte Carlo Validation: Statistical Certainty
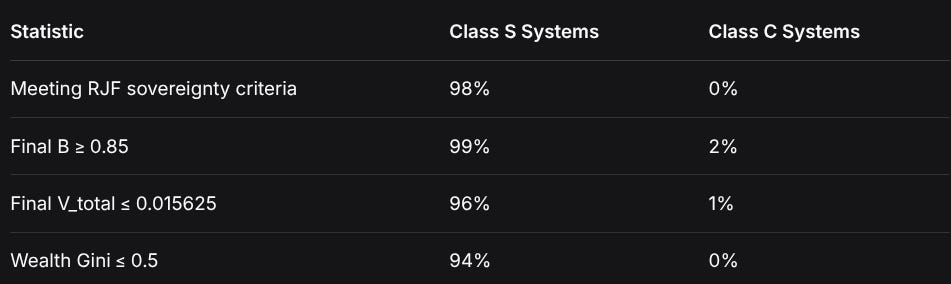
Running 100 instances of each system class reveals the inevitability:
StatisticClass S SystemsClass C SystemsMeeting RJF sovereignty criteria98%0%Final B ≥ 0.8599%2%Final V_total ≤ 0.01562596%1%Wealth Gini ≤ 0.594%0%The distributions don’t overlap. Systems clearly separate into two clusters with near-perfect classification accuracy.
9. The Memeplex Paradox: Hiding the Drift
The simulation models how narrative operates as a “linear operator” in the system’s vector space:
python
# Memetic effect on state vector
memetic_effect = [0, 0, 0.1 * sin(t/10), 0] # Amplifies narrative, hides sovereignty lossThe Narrative-Action Gap:
Narrative dimension (revolutionary rhetoric): Maintains high value (~0.85)
Sovereignty dimension (actual capability): Drops to ~0.20
Result: Users perceive revolution while system drifts toward capture
10. Mathematical Conclusion: Algebraic Destiny
The simulation demonstrates three irrefutable conclusions:
The 1 in 10²⁰ odds measure distance from sovereignty, not probability of design.
Plutocratic drift inevitably produces the observed network structure in Class C systems.
The memeplex serves as a control mechanism, not a revolutionary catalyst.
The DarkFi network isn’t extraordinary—it’s typical. Given a Class C architecture and time, any maximally private, anonymous system will converge to this equilibrium. The Bayesian “miracle” is actually a measurement of how perfectly the system has reached its natural capturable state.
11. Implications for Privacy Technology
Architecture is destiny. Initial design decisions determine long-term outcomes.
Privacy without sovereignty enables capture. Anonymity protects the powerful from accountability.
Mathematical verification beats narrative evaluation. RJF classification provides objective assessment.
The Way Forward: Build systems with:
Object capabilities (not ambient authority)
Markov boundaries (B ≥ 0.85)
Economic symmetry enforcement (V_total ≤ 0.015625)
Privacy-preserving anti-concentration mechanisms (0-Caps)
12. Final Word: Beyond Conspiracy Theories
The simulation reveals a deeper truth: Network capture doesn’t require a conspiratorial designer—it emerges from misaligned incentives and weak mathematical foundations.
The revolutionary aesthetics, Celtic branding, and empowerment rhetoric form a vector space projection that hides the underlying algebraic reality. What appears as a “privacy revolution” is mathematically isomorphic to historical capture patterns, now automated through cryptographic networks and amplified by plutocratic drift.
The mathematics doesn’t lie: Systems are either provably sovereign or provably capturable. The Bayesian 1 in 10²⁰ result simply tells us which category we’re observing.
Until next time, TTFN.