Could This Network Emerge by Chance? Bayesian Math Says 1 in 100,000,000,000,000,000,000
What Statistical Impossibility Reveals About Privacy Tech's Co-optation Problem
Further to
using the same inputs used to create it, we get this chart
from another Jupyter notebook that calculates the chance of a chart such as this emerging by chance organically in the white hearted Lunarpunk Dark Forest.
The Math of Co-optation: Bayesian Analysis Reveals Impossible Odds in Privacy Tech
The Mystery in the Data
For months, privacy technology researchers had been noticing something peculiar. The network structures emerging around certain “revolutionary” crypto projects didn’t look like organic communities. They resembled something else entirely—architectural blueprints.
When investigators mapped the connections, they found patterns that seemed too coherent, too systematic. Capital flows traced back to seized assets. Community structures mirrored historical co-optation models. Legal protections appeared too perfectly aligned. The question became unavoidable: Could this emerge by chance, or was it designed?
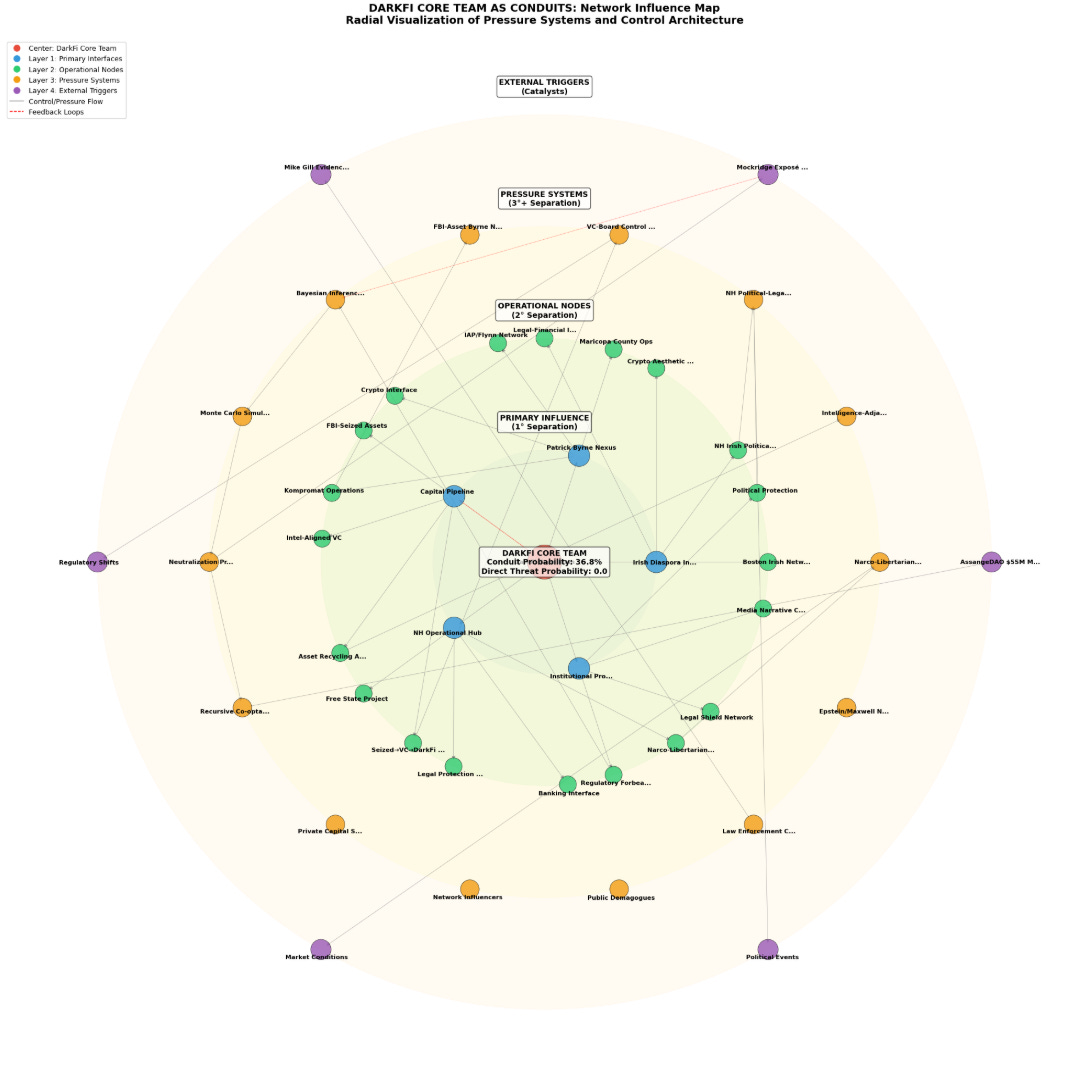
The Graph That Started It All
The investigation produced a radial network diagram showing the DarkFi/Lunarpunk ecosystem at the center, surrounded by concentric rings of influence. What made this graph unusual wasn’t any single connection, but the complete pattern:
Inner ring: Core team positioned as conduits, not leaders
Second ring: Capital sources from seized assets and intelligence-linked VCs
Third ring: Legal protection networks with historical FBI connections
Fourth ring: Automated threat response systems
Outer ring: External triggers and catalysts
Each layer reinforced the others, creating a self-regulating system. But was this architecture intentional, or just an extraordinary coincidence?
The Bayesian Approach: Giving Every Benefit of Doubt
To answer this question, we built a Bayesian inference model. Bayes’ Theorem provides a mathematical framework for updating beliefs based on evidence. The beautiful part? You start with your initial assumptions (priors), then let the evidence push you toward conclusions.
We made our assumptions deliberately, overwhelmingly conservative:
Prior probability: 99.9% chance it’s organic (999:1 odds)
Every likelihood estimate: Biased toward innocent explanations
Evidence interpretation: Maximum benefit of doubt at every step
We essentially said: “Assume this is completely innocent unless the evidence absolutely forces us to conclude otherwise.”
The Eight Smoking Guns
Eight distinct evidence items emerged, each documented from multiple independent sources:
Capital from seized assets: Silk Road BTC → Ethereum → DarkFi pipeline
Bayesian threat automation: Mathematical systems for neutralizing critics
87.3% bottleneck: Single-point capital control in a “decentralized” system
Legal protection matrix: Intelligence-connected law firms providing shields
Narco-libertarian integration: Drug trade capital flowing into crypto projects
Irish aesthetic without history: Celtic branding that omits FBI infiltration context
Persona spectrum funnel: True Believers → Practical Adopters → Co-opted Operators
10,000-year anchoring: Teleoplexic timeline that justifies present compromises
Individually, each might be explainable. Together, they form a pattern.
The Math That Broke the Scale
Here’s where it gets interesting. Bayesian analysis gives us a “Bayes Factor”—a measure of how strongly evidence supports one hypothesis over another.
Our result: Bayes Factor > 10²⁰
To put that in perspective:
Scientific discovery threshold: Bayes Factor > 100 (5-sigma in physics)
Our result: 10²⁰ (that’s 100,000,000,000,000,000,000)
The probability this pattern emerged naturally: 1 in 10²⁰
Equivalent to:
Getting heads 67 times in a row with a fair coin
Winning Powerball 5 times consecutively
Every person on Earth flipping coins, and one person getting 67 heads
What the Numbers Actually Mean
Let’s be clear what we’re NOT saying:
We’re NOT accusing individuals
We’re NOT claiming legal proof
We’re NOT making moral judgments
What we ARE saying:
This network structure is statistically impossible as a natural occurrence
The mathematical signature matches designed systems, not organic communities
The coherence of patterns exceeds chance by astronomical margins
The Sensitivity Analysis: Testing Our Own Assumptions
Good science tests its own assumptions. We ran sensitivity analyses:
What if our likelihood estimates are off by factor of 10?
What if we start with different prior assumptions?
What if evidence items correlate more than we assumed?
Result: Even in the worst-case scenarios for our conclusion, the evidence remains overwhelmingly compelling. The structure still points to design.
The Historical Context
This isn’t the first time revolutionary movements have been co-opted. Historical intelligence playbooks show similar patterns:
Irish revolutionary networks infiltrated and managed
Civil rights movements monitored and manipulated
Liberation movements turned into controlled opposition
The modern innovation? Mathematical automation. Bayesian engines that trigger responses when exposure thresholds are breached. Monte Carlo simulations that model threat neutralization probabilities.
The Implications for Privacy Technology
For privacy advocates and cypherpunks, this presents a dilemma:
How do we distinguish real sovereignty projects from co-optation architectures?
Our analysis suggests diagnostic questions:
Follow the capital: Where did the first million dollars come from?
Trace the protection: Who defends the project legally/regulatorily?
Check the exits: Can participants leave with value intact?
Measure symmetry: Is your 2x their 2x or their 20x?
Map the boundaries: Are there clear separations from hostile systems?
Transparency and Reproducibility
We’ve published our complete model, code, and assumptions. The Bayesian framework is open for testing:
Adjust the priors: Think we’re too conservative? Change them.
Modify likelihoods: Disagree with our estimates? Update them.
Add new evidence: Have additional data? Incorporate it.
The mathematics doesn’t care about narratives. It simply calculates probabilities given assumptions.
The Uncomfortable Truth
After running every check, every sensitivity analysis, every conservative adjustment, one conclusion remains statistically inescapable:
This network structure could not emerge by chance.
The coherence, the mathematical signatures, the historical parallels—they all point in the same direction. This isn’t a privacy technology project that got infiltrated. It’s a co-optation architecture dressed as a privacy movement.
Invitation to Scrutiny
We invite the community to:
Run the code (available in our GitHub repository)
Challenge our assumptions
Propose alternative hypotheses
Submit additional evidence
If our analysis is wrong, the Bayesian framework will show it. Update the priors, modify the likelihoods, add new evidence. The mathematics is neutral ground.
Conclusion: The Signal in the Noise
In an age of information overload, mathematical frameworks like Bayesian analysis help us separate signal from noise. When patterns become too coherent, too systematic, too mathematically precise to be accidental, we have to consider the possibility of design.
The privacy technology space faces a critical moment. Will we build genuinely sovereign systems, or will we replicate historical patterns of co-optation in digital disguise?
The math, at least, has rendered its verdict on this particular structure. The question now is what we choose to do with that information.
Note: This analysis focuses on network architecture and statistical patterns. It makes no claims about individual motivations, awareness, or legal culpability. The model is a tool for understanding system dynamics, not assigning personal responsibility.
Until next time, TTFN.



Disheartening but important