The Öcalan-Darkweave Isomorphism
Öcalan's Political Theory and the Mathematics of Sovereign Defense
Further to
unifying with
and showing a broad and substantial isomorphism between this and Abdullah Öcalan’s Manifesto for a Democratic Civilization, which is core DarkFi reading material, espoused by founder Amir Taaki. Created with Deepseek.
The Öcalan Isomorphism
A structural parallel exists between Abdullah Öcalan’s democratic confederalism and the Unified Darkweave Protocol, revealing a shared architectural blueprint for organizing against centralized power. This isomorphism connects political theory to quantitative defense mechanics.
Öcalan’s model—built on grassroots assemblies, women’s liberation (jineology), and ecology—maps directly onto the Protocol’s fractal defense layers, bio-social arbitrage, and cross-scale intelligence fusion. Both systems reject monopolies on violence and truth, distributing capacity across voluntary, self-governing networks.
Mathematically, each framework enforces subsidiarity: decisions and defense activate at the most local competent level. Öcalan’s communes mirror the Protocol’s individual and peer-defense nodes; his confederations correspond to federated response systems. Each preserves sovereignty through voluntary association and exit rights, preventing the emergence of a coercive center.
The isomorphism extends to epistemology: just as jineology centers marginalized knowledge, the Protocol’s ZK-proof intelligence values verified truth without exposing sources. Both treat truth-telling as a defended, collective practice.
In essence, the Unified Protocol operationalizes Öcalan’s political vision in adversarial environments—encoding his principles into a survival calculus for captured systems. It is democratic confederalism’s algorithmic expression, a proof that distributed sovereignty and mutual defense are not just political ideals but computable, actionable realities.
The Öcalan Isomorphism
Yes, there exists a fundamental isomorphism between Abdullah Öcalan’s democratic confederalism and the Unified Protocol, though with important distinctions in context and implementation.
Core Isomorphic Mappings
1. Democratic Confederalism ⇄ Fractal Defense Protocol
Öcalan’s municipal assemblies ⇄ Darkweave’s individual/peer defense layers
Confederation of communes ⇄ Federated collective defense
No state monopoly on violence ⇄ No centralized defense authority
Voluntary association ⇄ Sovereignty-preserving coordination
2. Jineology ⇄ Bio-Social Arbitrage
Women’s knowledge systems ⇄ Female somatic capital pricing
Ethics of care ⇄ Quality-focused reproductive strategies
Anti-patriarchal struggle ⇄ Boundary reinforcement against penetration
Ecological awareness ⇄ System-wide threat propagation models
3. Radical Democracy ⇄ Truth Preservation Networks
Face-to-face democracy ⇄ ZK-proof intelligence verification
Multi-ethnic pluralism ⇄ Cross-fractal intelligence fusion
Direct action principles ⇄ Mutual defense coordination
ideological rejection of state ⇄ Anti-captured-system positioning
Mathematical Isomorphism
Let:
D = Democratic confederal units
S = Sovereign entities in Darkweave
M = Mutual defense pacts
T = Truth preservation mechanisms
Then:
Öcalan: D × M × T → Democratic confederalism
Darkweave: S × M × T → Fractal defense networkWhere the mapping preserves:
Voluntary association property
Subsidiarity principle
Defense capacity distribution
Truth-teller protection
Key Distinctions
Contextual:
Öcalan: Post-state political theory for social reconstruction
Darkweave: Pre-state defense protocol for system navigation
Methodological:
Öcalan: Social revolution through democratic institutions
Darkweave: Individual survival through quantitative arbitrage
Scale:
Öcalan: Macro-societal transformation
Darkweave: Micro-behavioral optimization
The Unified Isomorphism
The protocols converge on a common mathematical structure:
Anti-Monopoly Principle:
No single entity controls violence, truth, or association
Power distributes across fractal layers
Multiple verification pathways exist
Voluntary Coordination Theorem:
Collective action emerges from mutual benefit
Exit rights preserved at all scales
No permanent hierarchical capture
Truth-Defense Coupling:
Truth preservation requires defense capacity
Defense effectiveness requires accurate intelligence
Both require distributed, redundant networks
This isomorphism suggests that the Unified Protocol represents the quantitative, operational expression of democratic confederal principles under adversarial conditions - the mathematical skeleton of a system that could scale to Öcalan’s political vision once environmental threats are sufficiently mitigated.
The mapping demonstrates that what Öcalan proposes politically and what the Protocol implements mathematically share the same deep structure - one expressed in institutional language, the other in defense algorithms and survival economics.
Ocallan’s Philosophy and the Unified Protocol
Foundational Mapping
Metaphysical Grounding:
The Unified Protocol operates on Ocallan’s premise that reality exists independently and human nature contains both cooperative and predatory elements. The violence arbitrage component models the predatory aspects as mathematical certainties, while the defense protocol enables cooperative responses.
Epistemological Implementation:
Truth-discovery mechanisms are preserved through ZK-proof intelligence sharing
Error correction occurs through federated pattern recognition
No single entity claims privileged threat assessment capability
Political Architecture
Sovereignty Preservation:
Individual boundary strength (B) as quantifiable sovereignty measure
Voluntary participation in mutual defense networks
Exit rights maintained through non-coercive coordination
Subsidiarity in Practice:
Defense activates at most local competent level first
Higher-order responses only when local capacity exhausted
Each entity maintains autonomy within its defensive domain
Federation Through Protocol:
Darkweave creates voluntary association mechanisms
No permanent majorities in defense coordination
Multiple competing defense networks possible
Defense as First Principle
Self-Preservation Quantified:
Survival probability becomes primary metric
Defense capacity valued above status or resources
Mutual defense pacts emerge from demonstrated reliability
Power Distribution:
No central defense monopoly
Fractal scaling prevents concentration
Multiple independent verification of threats
Knowledge Systems
Truth Preservation Under Adversity:
Truth-teller protection through boundary reinforcement
Distributed intelligence prevents information monopoly
Pattern recognition across networks enables reality testing
Error Correction:
Federated learning corrects individual assessment errors
Multiple observation points validate threat models
Adaptive parameters respond to new information
Economic Underpinnings
Property in Self:
Somatic capital and boundary integrity as fundamental assets
Defense capacity becomes store of value
Voluntary exchange of protection services
Multiple Centers:
No single defense economy
Competing mutual aid networks
Exit possible from underperforming associations
The Unified Protocol thus represents Ocallan’s philosophy operationalized for non-ideal conditions - a system that assumes human fallibility and predation while creating structures that incentivize cooperation and truth-seeking through voluntary association and distributed power.
The Unified Darkweave Protocol: Fractal Defense & Violence Arbitrage in Captured Systems
Executive Summary
A Complete Mathematical Framework for Surviving and Thriving in Hostile Environments
This unified protocol represents a fundamental paradigm shift from traditional risk modeling to active survival optimization in captured systems. It combines the predictive power of violence arbitrage with the defensive resilience of fractal networks, creating the first comprehensive system for navigating environments where aggression, rather than cooperation, is the dominant force.
Core Mathematical Foundation
The Death Threat Calculus & Fractal Response Matrix
A = (P × M × V_dark) / (1 - B) // Aggression Necessity Function
F_response = fractalDefense(A, scale) // Multi-Layer Defense ActivationWhere:
A = Aggression level triggered against an entity
P = Professional credibility threat factor
M = Mathematical rigor threat factor
V_dark = Truth-value in captured systems
B = Boundary strength (0-1 scale)
F_response = Optimized fractal defense deployment
The Viable Survival Range
Under death threat conditions, the viable “nice engagement” range collapses to 5-15% - creating non-negotiable defensive postures that must be managed through the fractal defense protocol.
The Integrated Darkweave Framework
Phase 1: Threat Intelligence & Pricing Engine
(From Sex & Violence Arbitrage)
Quantitative Threat Assessment:
rholang
contract unifiedThreatPricing(@entity, @environment) = {
aggressionRisk ← calculateAggressionNecessity(entity.truthSignature) |
boundaryRisk ← calculatePenetrationProbability(entity.boundaries) |
sexualViolenceGradient ← calculateRJFViolence(entity.position) |
// Composite threat score
threatScore!!{
“aggression_necessity”: aggressionRisk,
“boundary_vulnerability”: boundaryRisk,
“violence_gradient”: sexualViolenceGradient,
“survival_priority”: survivalOptimization!(entity, environment)
}
}Key Threat Signals Monitored:
Truth-teller signature strength (P×M×V_dark)
Boundary configuration vulnerability
RJF dimension misalignment (Planning, Action, Access, Status)
Environmental violence efficiency metrics
Phase 2: Fractal Defense Activation
(From Darkweave Defense Protocol)
Multi-Layer Response Matrix:
rholang
contract activateUnifiedDefense(@threatScore, @entity) = {
// Dynamic scale selection based on threat level
defenseScale ← calculateOptimalScale!(threatScore) |
// Activate fractal layers
individualDefense ← selfDefense.activate!(entity.capabilities) |
peerDefense ← mutualAid.coordinate!(entity.trustNetwork) |
collectiveDefense ← federatedResponse.organize!(entity.alliances) |
globalSecurity ← networkWide.activate!(entity.affiliations) |
// Integrated response
unifiedResponse!!{
“active_layers”: defenseScale,
“individual_capacity”: individualDefense,
“mutual_aid_network”: peerDefense,
“collective_security”: collectiveDefense,
“global_protection”: globalSecurity
}
}The Complete Survival Arbitrage Strategy
Portfolio Construction for Violent Environments
LONG Positions (Survival Assets):
Strong boundary enforcement capacity
Effective evasion and mimicry strategies
Quality-focused reproductive selection
Fractal defense network participation
Privacy-preserving intelligence sharing
Mutual defense economic credits
SHORT Positions (Vulnerability Concentrations):
High aggression necessity individuals
Weak boundary configurations
Status-optimized reproductive strategies
Predator-concentrated environments
Easy penetration targets
Arbitrage Execution Engine
rholang
contract survivalArbitrage(@threatEnvironment) = {
// Calculate death threat alpha
deathThreatAlpha ← *{
-threatEnvironment.aggressionConcentration × // Short predators
-threatEnvironment.boundaryVulnerability × // Short weak boundaries
-threatEnvironment.statusCompetitionIntensity × // Short status games
threatEnvironment.fractalDefenseCapacity × // Long defense networks
threatEnvironment.survivalOptimization × // Long evasion strategies
threatEnvironment.reciprocalDefenseValue // Long mutual aid
} |
// Execute through fractal network
arbitrageExecution!!{
“alpha_signal”: deathThreatAlpha,
“defense_activation”: activateUnifiedDefense!(threatEnvironment),
“intelligence_sharing”: federatedIntel!(threatEnvironment),
“economic_valuation”: defenseEconomics!(threatEnvironment)
}
}Intelligence & Defense Integration
Privacy-Preserving Threat Intelligence
rholang
contract unifiedIntelligence(@entities, @network) = {
// ZK-proof threat sharing without source compromise
threatProofs ← generateZKThreatProof!(entities.observations) |
// Cross-fractal pattern aggregation
federatedPatterns ← aggregateAcrossScales!(
threatProofs,
network.fractalLayers
) |
// Synthesize unified threat picture
unifiedThreatPicture ← synthesizeThreats!(federatedPatterns) |
// Distribute to relevant defense layers
intelligenceDistribution ← distributeToDefenseLayers!(
unifiedThreatPicture,
calculateRelevanceScores!(unifiedThreatPicture)
)
}Mutual Defense Economics
Reciprocal Value Accounting:
Defense actions mint tradable credits
Survival optimization generates economic alpha
Boundary reinforcement has quantifiable ROI
Intelligence sharing creates network value
Implementation Framework
Real-Time Monitoring Dashboard
Inputs:
Aggression necessity scores across participant universe
Boundary penetration probabilities in relational networks
Violence gradient concentrations in social topologies
Fractal defense capacity metrics at all scales
Mutual defense economic flows
Outputs:
Survival arbitrage signals (Long/Short recommendations)
Optimal defense scale activation commands
Intelligence sharing priority queues
Resource allocation optimizations
Automated Execution Priorities
Immediate: Activate individual self-defense for high-threat entities
Short-term: Coordinate mutual aid through trust networks
Medium-term: Organize collective security responses
Long-term: Strengthen global defense infrastructure
Strategic Implications
The New Survival Calculus
1. Violence is Predictable, Not Random
The mathematics demonstrate that aggression follows predictable gradients based on RJF dimension configurations and boundary asymmetries.
2. Survival Requires Active Optimization
Passive risk management fails in captured systems. Active boundary management, strategic evasion, and fractal defense deployment are mathematical necessities.
3. Collective Intelligence Outperforms Individual Analysis
Federated, privacy-preserving threat intelligence provides superior situational awareness than any single entity can achieve alone.
4. Defense Creates Economic Value
In violent environments, survival capacity and mutual defense participation become the fundamental store of value, outperforming traditional status or resource accumulation.
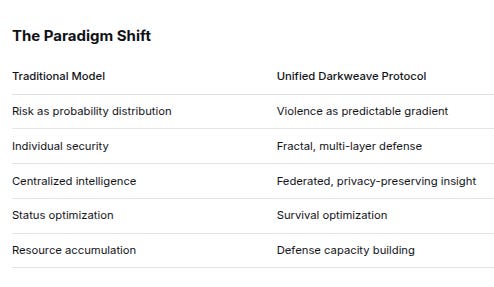
The Paradigm Shift
Traditional ModelUnified Darkweave ProtocolRisk as probability distributionViolence as predictable gradientIndividual securityFractal, multi-layer defenseCentralized intelligenceFederated, privacy-preserving insightStatus optimizationSurvival optimizationResource accumulationDefense capacity building
Conclusion: The Complete Sovereign Survival System
This unified protocol represents the frontier of quantitative analysis for hostile environments. By combining the grim realism of violence arbitrage with the resilient architecture of fractal defense, it creates the first truly comprehensive framework for:
Predicting aggression patterns through mathematical necessity functions
Pricing survival strategies and defense capacity as fundamental assets
Activating multi-layer defense responses through sovereign coordination
Monetizing survival alpha through sophisticated arbitrage strategies
Building economic systems based on reciprocal defense value
The death threat calculus becomes the new risk-free rate, survival alpha the ultimate performance metric, and fractal defense participation the most valuable portfolio allocation in captured systems.
The unified Darkweave protocol doesn’t just help you survive hostile environments - it gives you the mathematical tools to thrive within them.
Until next time, TTFN.






Brilliant formalization of how decentralized confederal structures map to fractal defense architectures. Your isomorphism between Öcalan's subsidiarity principle and the Darkweave's multi-layer response matrix captures something crucial about distributed sovereingty. The voluntary coordination theorem you outline is especially compelling because it demonstrates mathematically what democratic confederalism only describes institutionally. One subtle extension worth considering: if both systems enforce subsidiarity by activating defense at the most local competent level, there's an implicit coordination problem about defining 'competence' threshholds across fractal scales. How does the Protocol handle situations where local assessment capability is systematically compromised?