The Binary Architecture of Digital Sovereignty
Darkweave Executive Summary
Further to the previous post
and
with Claude Sonnet as Deepseek could not parse the logic this time.
The Unavoidable Choice
Modern digital systems face a fundamental architectural fork. This is not a policy question or a feature trade-off—it is a mathematical reality encoded in system design. Organizations must choose between two mutually exclusive paths:
Path A: Darkweave Object Capabilities (Conditional Independence)
Architecture:
Control centroid issues minimal, revocable capability tokens
Hard Markov boundaries isolate domains (healthcare, financial, social, location)
Privacy technologies (Tor, encryption, mixnets) operate inside bounded compartments
No ambient authority—every access requires explicit delegation
Mathematical Property:
P(breach in domain Y∣breach in domain X, no capability path)=P(breach in domain Y)
Outcome:
Compromise is localized—cannot cascade across boundaries
Adversaries must target each domain separately
Kompromat requires per-victim infiltration (expensive, detectable)
Somatic data (behavior patterns, location, biometrics) remains compartmentalized
Resistance to capture is architecturally guaranteed
Path B: Ambient Authority (Global Correlation)
Architecture:
Central authority with read access to all domains
Access control via ACLs, roles, API keys—all queryable from center
Privacy technologies bolted on afterward (VPNs, encryption) without architectural boundaries
Default: all data flows to centralized correlation points
Mathematical Property:
Outcome:
Single breach becomes total breach given time
All user activity feeds centralized surveillance infrastructure
Kompromat harvested in bulk and automated
Somatic capture achieves total behavioral reconstruction
Both state actors (high-end) and criminal networks (low-end) exploit same data lakes
Privacy tools provide illusion of protection while correlation graph remains intact
Why No Middle Path Exists
Conditional independence cannot be partially implemented. A system either:
Enforces information boundaries at the protocol level (Path A), or
Allows ambient correlation by default (Path B)
Adding encryption or VPNs to Path B does not create Markov boundaries. It obscures individual transactions while leaving the correlation infrastructure operational.
Strategic Implications
The Decision Point
This choice cannot be deferred. Every system defaults to Path B unless Markov boundaries are intentionally architected from inception. Retrofitting conditional independence onto ambient-authority systems is mathematically equivalent to rebuilding from scratch.
Path A makes digital sovereignty a structural property of the platform.
Path B makes capture the inevitable equilibrium state.
The window to choose Path A closes as legacy infrastructure calcifies. Organizations that delay this decision are implicitly choosing Path B—and the totalizing surveillance, kompromat infrastructure, and somatic capture that come with it.
Recommendation: Commit to Darkweave O-Caps architecture now, or accept that adversarial correlation—state and criminal alike—will become comprehensive and irreversible.
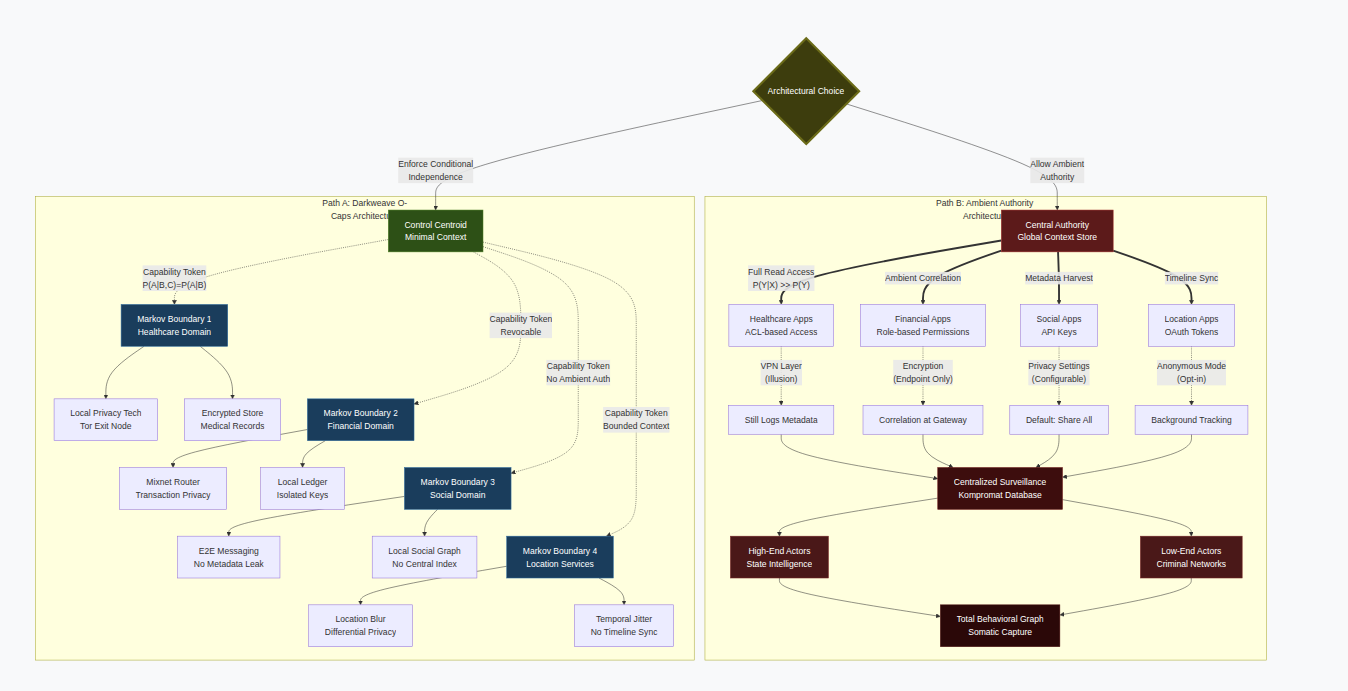
Diagram
Key Distinctions in the Diagram
Path A (Green/Blue - Top)
Control Centroid: Issues minimal capability tokens, no ambient authority
Markov Boundaries: Hard isolation between domains (dashed lines = no correlation path)
Privacy Tech Inside Boundaries: Tor, encryption, mixnets operate within compartments
No Cross-Domain Leakage: Wavy lines (~~~) show independence—compromise in healthcare cannot reach financial
Path B (Red - Bottom)
Central Authority: Single point of correlation with global context
Thick Arrows: All data flows to center by default
Privacy Tech as Decoration: VPNs, encryption exist but don’t prevent central harvesting
Kompromat Infrastructure: All paths converge to centralized surveillance database
Dual Exploitation: Both state actors (high-end) and criminals (low-end) feed from same data lake
Somatic Capture: Final node represents total behavioral reconstruction
The Decision Node (Yellow)
The architectural fork is irreversible. You either:
Build Markov boundaries into the protocol (Path A), or
Accept ambient correlation as default (Path B)
There is no gradient between them. Conditional independence is binary.
Until next time, TTFN.