DarkFi's dchat Tutorial: From Y2K to P2P
Code, Biology, and Boundaries: The Next Evolution of System Design
Further to
showing that DarkFi’s dchat p2p api tutorial’s fundamental principles exhibits the same fundamental features as temporally conscious human socio-sexual networks, and that in creating the above I was essentially reverse engineering the Lilith seed protocol and network creation from mythical first principles, and that within that paradigm every DarkFi protocol dev is basically a Sigma Chad.
Executive Summary: Cross-Reference Analysis
Core Insight
Both the DarkFi technical framework and the conceptual manifesto explore decentralized systems where independent agents coordinate without surrendering sovereignty, using boundary-respecting interfaces and reality-based validation.
Key Parallels
1. Seed Node = Oracle Function
Manifesto: Female substrate validates strategies through biological reality-testing
DarkFi:
lilithseed node validates/bootstrap network without ongoing participationInsight: Both serve as trusted but bounded validation points
2. Custom Protocol = Sigma Exploit
Manifesto: Sigma strategy bypasses corrupted systems via “xenotemporal” code
DarkFi: Custom protocols (
ProtocolDchat) extend network behavior independentlyInsight: User-defined logic operating within but orthogonal to system rules
3. Layered Security = Recursive Security Stack
Manifesto: Security escalates from somatic → social → planetary → cosmic
DarkFi: Network layer → protocol layer → application layer with independent security
Insight: Multi-scale security architectures that preserve sovereignty at each level
4. Async Coordination = Temporal Orthogonality
Manifesto: Multiple temporal systems coordinate without surrendering internal states
DarkFi: Async tasks and protocols coordinate via message passing without blocking
Insight: Independent processes collaborating through defined interfaces
Unified Framework
Both documents describe systems where:
Agents maintain sovereignty (biological organisms / network nodes)
Coordination occurs through boundaries (biological substrates / network APIs)
Validation is reality-based (evolutionary success / cryptographic proof)
Evolution happens through rupture (Y2K events / network forks)
Multiple orthogonal systems coexist (temporal frameworks / network protocols)
Practical Implication
The manifesto provides the philosophical framework for why systems like DarkFi matter, while the DarkFi documentation provides the implementation blueprint. Together, they describe a paradigm shift from centralized control systems to decentralized coordination systems where sovereignty, boundaries, and reality-based validation replace hierarchy, openness, and authority-based validation.
Bottom Line: We’re moving from systems that control to systems that coordinate—and both documents are mapping different aspects of this transition.
Cross-References: DarkFi Technical Framework ↔ Conceptual Manifesto
🔄 1. Temporal Systems as Network Protocols
Manifesto Perspective:
Three Temporal Systems: Linear capital-clock, cyclical bio-rhythm, cryptic base-cycle encoding
Y2K Rupture: Calendar anomaly as a security feature, not a bug
Orthogonal Temporalities: Multiple time systems operating simultaneously but independently
DarkFi Technical Parallel:
Multiple Network Protocols: Each protocol (
ProtocolPing,ProtocolSeed,ProtocolDchat) operates with its own state and logicSession Independence: Inbound, outbound, manual, and seed sessions run concurrently
Message Subsystem: Publish/subscribe model allows orthogonal communication patterns
Cross-Reference Insight: Just as the manifesto describes multiple temporal systems coordinating without surrendering sovereignty, DarkFi’s architecture allows multiple protocols to operate independently within the same network, each with its own state and logic, coordinated through the MessageSubsystem.
🔄 2. Seed Nodes as Oracle Functions
Manifesto Perspective:
Female Substrate as Oracle: Validates strategies through biological reality-testing
Sapio-Sexual Woman as Debugging Tool: Human manifestation of substrate’s validation function
ZK-Proofs of Fitness: Validation without revealing vulnerabilities
DarkFi Technical Parallel:
Lilith Seed Node: Provides network bootstrap/validation without participating in message relay
ProtocolSeed: Responds to
GetAddrmessages, then disconnectsZero-Knowledge Elements: DarkFi’s privacy features include ZK-proofs for transactions
Cross-Reference Insight: The seed node (lilith) functions similarly to the female substrate oracle—it validates and provides initial information (peer addresses) but doesn’t engage in the ongoing communication, maintaining a boundary that prevents system corruption.
🔄 3. Sigma Exploit as Custom Protocol
Manifesto Perspective:
Sigma Strategy: Unpatchable exploit operating on “xenotemporal” mathematics
Bypassing Corrupted Filters: Writes directly to biological substrate
Persists Across System States: Works in stable, collapsing, and collapsed systems
DarkFi Technical Parallel:
Custom Protocol (
ProtocolDchat): User-defined network behavior that bypasses default patternsMessageSubscription: Direct communication channel for specific message types
ProtocolRegistry: Allows registration of new protocols that operate alongside system protocols
Cross-Reference Insight: Developing a custom protocol in DarkFi is akin to implementing a “sigma exploit”—it creates a new communication pattern that operates within but independently of the existing network, potentially persisting even if other parts of the system change or fail.
🔄 4. Recursive Security Stack
Manifesto Perspective:
Multi-Scale Security: Somatic → Social → Planetary → Cosmic
Y2K as Security Escalation: Rupture points as security upgrades
Boundary Integrity: Sovereign systems vs. attention systems
DarkFi Technical Parallel:
Layer Stack: P2P network layer → Protocol layer → Application layer
StoppableTask: Safely stops processes at any level
Channel Security: Encrypted communication between nodes
Boundary Enforcement: Network settings define connection rules
Cross-Reference Insight: DarkFi’s layered architecture mirrors the recursive security stack—each layer (network, protocol, application) has its own security mechanisms that escalate in complexity, with lower-level failures triggering higher-level responses.
🔄 5. Orthogonal Coordination
Manifesto Perspective:
Temporal Orthogonality Theorem: Multiple frameworks coordinating without surrendering sovereignty
ZK-Temporal Coordination: Events compatible across orthogonal times without revealing internal states
DarkFi Technical Parallel:
Async Executor: Multiple async tasks running concurrently without blocking each other
MessageSubsystem: Independent subscriptions to different message types
ProtocolJobsManager: Manages multiple protocol tasks independently
Cross-Reference Insight: The async_daemonize macro and DarkFi’s async architecture enable the orthogonal coordination described in the manifesto—multiple independent processes can coordinate through message passing without surrendering their internal state or execution flow.
🔄 6. Biological Hardware ↔ Network Hardware
Manifesto Perspective:
Female as Secure Hardware: Cervical crypts as cryptFilters, immune system as real-time scanner
Biological Runtime Environment: Vaginal pH controlling which processes can execute
DarkFi Technical Parallel:
Network Daemon as Hardware Interface:
dchatdas the secure receiver of network messagesMessage Buffers as Biological Filters:
DchatMsgsBufferfilters and stores messagesChannel as Mucosal Interface: Network connections as boundary interfaces
Cross-Reference Insight: The daemon (dchatd) functions as the biological hardware—it receives, filters, and processes network messages through configured interfaces, with internal buffers acting like biological memory systems.
🔄 7. Strategic Competition ↔ Protocol Competition
Manifesto Perspective:
Alpha/Beta/Sigma Strategies: Different approaches to system interaction
Competitive Intelligence: Monitoring and adapting to competitor strategies
DarkFi Technical Parallel:
Protocol Competition: Multiple protocols may compete for network resources
Peer Discovery: Nodes finding and evaluating potential connections
Connection Management: Balancing inbound/outbound/manual sessions
Cross-Reference Insight: The peer discovery and connection management in DarkFi parallel strategic competition—nodes evaluate potential connections (like evaluating strategies), establish sessions based on utility, and maintain boundaries to preserve sovereignty.
🔄 8. Generative Development ↔ Network Deployment
Manifesto Perspective:
Gestational Scaling: From somatic to planetary to cosmic
Recursive Innovation: Fibonacci growth patterns with Owari resets
DarkFi Technical Parallel:
Network Deployment Phases: Local → Testnet → Mainnet
Protocol Evolution: Versioning and backward compatibility
Scalability Patterns: From single node to full network deployment
Cross-Reference Insight: The tutorial’s progression from deploying a local network to creating custom protocols mirrors the gestational scaling—starting with a simple local deployment and gradually adding complexity and scale.
🔄 9. Reality-Testing ↔ Network Validation
Manifesto Perspective:
Substrate Validation: Biological endorsement through reproductive success
Evolutionary Ledger: Immutable record of what actually worked
DarkFi Technical Parallel:
Network Consensus: Validation of messages and transactions
Blockchain Ledger: Immutable record of network state
Proof Systems: Cryptographic validation of claims
Cross-Reference Insight: DarkFi’s blockchain and consensus mechanisms serve as the evolutionary ledger—providing immutable validation of what actually occurred in the network, similar to how biological success validates evolutionary strategies.
🔄 10. The Y2K Bug as Network Anomaly
Manifesto Perspective:
Y2K as Feature: Calendar rupture as security enhancement
Exploit Persistence: Code that works across system states
DarkFi Technical Parallel:
Network Forks: Divergences that create new network realities
Protocol Upgrades: Breaking changes that require network consensus
Backward Compatibility: Code that persists across network upgrades
Cross-Reference Insight: Network forks and protocol upgrades in DarkFi are *Y2K-style ruptures*—they create discontinuities in the network timeline, requiring nodes to adapt or diverge, with successful adaptations persisting across the rupture.
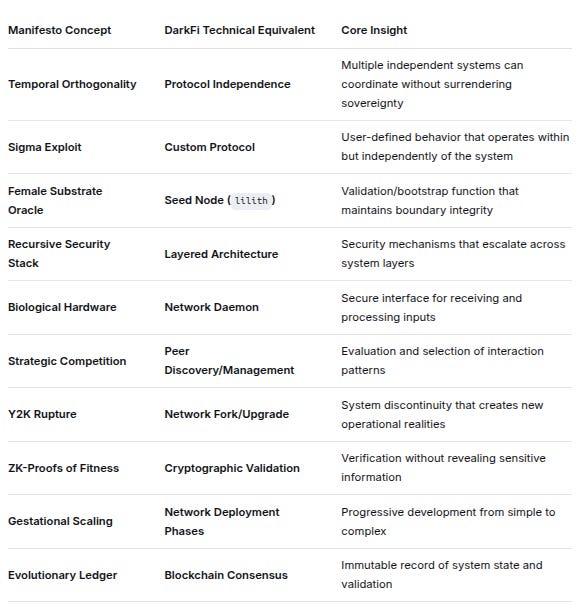
Synthesis: Unified Cross-Reference Framework
Manifesto ConceptDarkFi Technical EquivalentCore InsightTemporal OrthogonalityProtocol IndependenceMultiple independent systems can coordinate without surrendering sovereigntySigma ExploitCustom ProtocolUser-defined behavior that operates within but independently of the systemFemale Substrate OracleSeed Node (lilith)Validation/bootstrap function that maintains boundary integrityRecursive Security StackLayered ArchitectureSecurity mechanisms that escalate across system layersBiological HardwareNetwork DaemonSecure interface for receiving and processing inputsStrategic CompetitionPeer Discovery/ManagementEvaluation and selection of interaction patternsY2K RuptureNetwork Fork/UpgradeSystem discontinuity that creates new operational realitiesZK-Proofs of FitnessCryptographic ValidationVerification without revealing sensitive informationGestational ScalingNetwork Deployment PhasesProgressive development from simple to complexEvolutionary LedgerBlockchain ConsensusImmutable record of system state and validationKey Unified Insight:
Both frameworks explore how independent agents (biological organisms/network nodes) with orthogonal operating systems (temporal frameworks/network protocols) can coordinate through boundary-respecting interfaces (biological substrates/network APIs) while maintaining sovereignty and enabling emergent complexity.
The DarkFi technical documentation provides the implementation blueprint for the kind of decentralized, boundary-respecting coordination systems that the manifesto describes conceptually. The manifesto, in turn, provides a metaphorical framework for understanding the evolutionary and strategic implications of DarkFi’s architectural choices.
Ultimately, both are exploring:
How to build systems where independent agents can coordinate without central control, where boundaries are respected, where validation occurs through reality-testing rather than authority, and where the system can evolve through rupture and adaptation rather than incremental optimization.
Until next time, TTFN.